Backdoor: Difference between revisions
No edit summary |
(→Output: changed date of recording to show it was day before lunch with Kurt.) |
||
| Line 1,312: | Line 1,312: | ||
::'''Audio:''' [[Media:Backdoor_audio_30.mp3|MP3 file]] | ::'''Audio:''' [[Media:Backdoor_audio_30.mp3|MP3 file]] | ||
::'''Estimated Recording Date:''' | ::'''Estimated Recording Date:''' July 25th based on her [http://thepathofleasttime.com/archives/2005/07/planes_and_date.htmllunch date with Kurt] which we know was on July 26th | ||
::'''Transcription:''' | ::'''Transcription:''' | ||
Revision as of 20:06, 15 September 2006
This page describes the Academy's Crypto Department Backdoor file system. The system was used to discover a set of discussions and a parts list, as compiled by Karen Moro. Please see the Backdoor Summary page, which is simply a collection of the important facts learned from this endeavour. Those wanting to understand the mechanics behind the Backdoor (and help resolve some unsolved questions) should read the Backdoor Primer.
Summary
Note: after the shut down of the data link to Earth, which was restored at the San Francisco live event, this page is not accessible. Not known if it will come back up.
After discovering that V called someone at the Academy's Crypto Department, Caine heads over to Crypto to investigate. He runs into his friend Neville Clark, who is talkative, if obfuscating. The Cube Hunters entice Nev into sharing more information by giving him a puzzle, designed by jbd and written by Scott, to solve. Nev takes the bait, and gives us a backdoor that leads to a gridded file system.
Dragging the commands onto the grid to create various configurations yields a series of log snippets. Some of the logs resemble the Perplex City Errorlogs that were found before the puzzle cards were released.
The interface could be accessed at the following URL:
http://events.perplexcity.com/gateway/commandinterface/index.html
As of 19 July 2006, the puzzle appears to be sifted through entirely and exhausted. For those new to it, or just generally confused, see the Backdoor Primer to learn how the interface operates.
If you simply don't have time or interest to sort through this entire page, you are welcome to read the Backdoor Summary page, which collects the audio transcriptions and inventory catalogues. It's the very short version of all this.
Commands
Through the combined work of jalapenodude, pelrun, and jbd, #syzygy has determined that the commands appear to work as follows.
The program pointer starts with the highest command in the left-hand column. It moves through the grid one space at a time, as determined by the command in that space and which spaces have been used before.
Generally, the pointer moves in the following directions when it encounters each command. However, if the next square has already been "used", the next direction (listed in brackets) is attempted. If this square has already been used, then the next in the list will be tried, and so on and so on (although N.B. the list of these below is far from complete). Some exceptions to this may occur - possibly certain combinations of commands may not run this check?
mount - se
zone - west (but then see grid below, as seems to vary)
switch - se (...) (''Are you sure, goes NE on config 5 below?'')
rotate - north (northeast, then in clockwise order?)
copy - south (...)
flush - south (southeast, ...)
pwrite - e (south, ...)
popen - east (south, ...)
pread - west (south, ...)
(This means the grids below are dependent on what commands were used to reach a particular square... But I'll leave it here for the time being -- Scribe.)
End, if executed before a MOUNT command, will "log out" of one of two accounts. Configuring the system is different for no end commands, one end command, or two end commands. After MOUNT, END will end execution with the error "session can not be unloaded at this time". It is good for testing where the code is going.
Cache seems to only work as an end point. Run can go anywhere that the program pointer isn't reaching.
A configuration is a set of commands placed on the grid so that the grid is valid and a log file is retrieved. The command path is the actual path that the pointer takes through the grid configuration. Different configurations may break down into the same command path.
Configurations and command paths start with ZO-MO, and usually end with either CACHE or FLUSH.
Furthermore, commands are time-sensitive. The same command path may yield a different result depending on the time it operates. This realization came after most of the command path additions within this entry. Therefore, great care must be taken to not only log the times that one accesses any bit of information using a specific command code, but to also go back and check for new paths especially since it seems some Audio files are only accesible using a single command code at a specific time.
Full Command Path List
The first two numbers are the resulting configuration, the letter after is the variation, and the string is the command path, with each instruction cut to two letters in length. The list is alphabetized based on operation name, as a reference service. Please be sure to also place them above with their respective results, and to sort them in properly when added.
08B ZO-MO-CO-PR-RO-RO-SW-SW-RO-CA 06A ZO-MO-CO-PW-RO-SW-RO-FL 01B ZO-MO-CO-RO-RO-RO-RO-RO-ZO-CA 03C ZO-MO-MO-SW-RO-CA 02B ZO-MO-PO-RO-PW-CA 02A ZO-MO-PO-RO-RO-RO-CA 03A ZO-MO-PO-RO-SW-CA 01A ZO-MO-PO-ZO-RO-RO-CA 13A ZO-MO-PR-PR-CO-CO-PW-RO-SW-SW-RO-CA 11A ZO-MO-PR-PR-SW-SW-SW-RO-SW-RO-CA 08A ZO-MO-PR-SW-SW-RO-CA 09A ZO-MO-PR-SW-SW-SW-RO-CA 10A ZO-MO-PR-SW-SW-SW-RO-RO-CA 07A ZO-MO-PW-RO-SW-FL-ZO-CA 06B ZO-MO-PW-RO-SW-RO-FL 02C ZO-MO-RO-CA 03B ZO-MO-SW-RO-CA 18A ZO-MO-SW-SW-ZO-ZO-ZO-PR-CA 12A ZO-MO-ZO-CO-PW-SW-RO-RO-SW-CA 19A ZO-MO-ZO-SW-SW-SW-SW-RO-RO-CA 20A ZO-MO-ZO-SW-SW-SW-SW-RO-RO-RO-CA 04A ZO-MO-ZO-ZO-CO-CO-CO-RO-RO-PW-RO-CA 05A ZO-MO-ZO-ZO-CO-CO-CO-SW-RO-PW-RO-CA 16A ZO-MO-ZO-ZO-PW-RO-SW-PR-CA 15A ZO-MO-ZO-ZO-SW-SW-SW-RO-CA 14A ZO-MO-ZO-ZO-SW-SW-SW-RO-SW-RO-CA 17A ZO-MO-ZO-ZO-ZO-PW-RO-SW-CA
Command/File Mapping
The number of times the end, zone, switch, and rotate commands appears in a command path determines which file is displayed.
Zero ENDs
| switch | ||||||
|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | ||
| rotate | ||||||
| 1 | master | TNI | Suspic. | Header | Ioniser | |
| 2 | unread | TNI | Yorke | NanoImg | Ioniser | |
| 3 | master | TNI | Suspic. | Header | Ioniser | |
| 4 | unread | TNI | Yorke | NanoImg | Ioniser | |
| switch | ||||||
|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | ||
| rotate | ||||||
| 1 | Camera | Coffee | Noise Control | NanoImg | unread | |
| 2 | Camera | Coffee | Noise Control | NanoImg | Tajison | |
| 3 | Camera | Coffee | Noise Control | NanoImg | Battery | |
| 4 | Camera | Coffee | Noise Control | NanoImg | unread | |
| switch | ||||||
|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | ||
| rotate | ||||||
| 1 | Laser | Sphere | unable | Clock | MagReg | |
| 2 | unread | Sphere | unable | Clock | MagReg | |
| 3 | Laser | Sphere | unable | Clock | MagReg | |
| 4 | unread | Sphere | unable | Clock | MagReg | |
| switch | ||||||
|---|---|---|---|---|---|---|
| 0 | 1 | 2 | 3 | 4 | ||
| rotate | ||||||
| 1 | unread | RNG | WHISK | unread | unread | |
| 2 | unread | RNG | WHISK | unread | unread | |
| 3 | unread | RNG | WHISK | unread | unread | |
| 4 | unread | unread | WHISK | unread | unread | |
One END
So far these have just produced single letters/characters. We're not sure if this is affected by Zones/Switches/Rotates, or by the Pwrite/Preads yet, so full configs are listed below:
n
Grid: E Z Sw - -/ - Ca Pr Mo -/ - -Ro Fl Zo/ - -Ro Ro Pr/ - - Ro Z Z
Command path: En Zo Sw Mo Zo Fl Ro Pr Zo Zo Ro Ro Ro Pr Ca
Total Zo/Sw/Ro: 4 Zo, 1 Sw, 4 Ro
' (apostrophe)
Grid: - - Ca Pr -/E Mo - Ro Pr/ - - S Pw Ro/ - - Ro Pw Pw/ - - Ro Z Z
Command path: En Mo Sw Pw Pw Zo Zo Ro Ro Pw Ro Pr Ro Pr Ca
Total Zo/Sw/Ro: 2 Zo, 1 Sw, 4 Ro
h
Grid: E M - - -/ - - Sw Ca Pr/ - - Pw Z Ro/ - - Ro Pr Ro/ - - - Ro -
Command path: En Mo Sw Zo Pw Ro Pr Ro Ro Ro Pr Ca
Total Zo/Sw/Ro: 1 Zo, 1 Sw, 4 Ro
n (second one? or the same?)
Grid: En Mo - - - / - - Sw - - / Pw Zo Zo Zo Pr / Ro Pr Ro Ro Ca / - Ro - - -
Command path: En Mo Sw Zo Zo Zo Pw Ro Pr Ro Ro Ro Pr Ca
Total Zo/Sw/Ro: 3 Zo, 1 Sw, 4 Ro
Two ENDs
The following tables are for the userspace files once 2 END commands have been introduced. So far, it looks like there's only 1 zone, no switches, and either 1 or 2 rotates depending on the time. The files available switch every 3-4 hours, and the table below assumes they switch on the hour but this may be wrong. Times are all in UTC/GMT.
Ah. There seems to be a clash already. Maybe the changeover is more random than we thought?
| Time (UTC/GMT) | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0000 | 0100 | 0200 | 0300 | 0400 | 0500 | 0600 | 0700 | 0800 | 0900 | 1000 | 1100 | ||
| rotates | |||||||||||||
| 1 | ? | ? | ? | ? | ? | ? | ? | ? | ? | over and out (0923) | ? | ? | |
| 2 | ? | ? | ? | ? | ? | ? | ? | ? | ? | todo (0921) | ? | ? | |
| Time (UTC/GMT) | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | 1300 | 1400 | 1500 | 1600 | 1700 | 1800 | 1900 | 2000 | 2100 | 2200 | 2300 | ||
| rotates | |||||||||||||
| 1 | ? | ? | ? | ? | 14-jul | 14-jul | 14-jul (1820) | drinks (1910, 1923) themes (1920) |
themes | themes | todo2 | ? | |
| 2 | ? | ? | ? | ? | 14-jul | 14-jul | 14-jul (1820) | drinks (1910) | ? | ? | case gone | ? | |
Errors
Lovingly stolen from SteveC's forum post...
"No disk access" - you didn't put a mount in
"Timeout in Folder" - you didn't put a rotate in
"no area has been accessed": You didn't put a zone in
"Unable to reset read permission" - misuse of pread
"Unable to write to file" - misuse of flush
"Unable to reset open permissions": misuse of popen
"Unable to access file" - empty/corrupt location
"Unable to get read handle" - empty/corrupt location<>br>
"Session cannot be unloaded at this time" - You put an end in AFTER a mount
"All login sessions ended: File server inactive" - you put END END END before the mount
"File access denied" - you put run in the path at the end, not cache.
Infinite Loops
Certain configurations get into endless loops, causing the interface to crash and throw up random data (see Gatehouse logs. Direction is important in causing these, but some commands seem more "crash-friendly" than others. Working out which ones can cause loops may help in finding how Caine broke the system] a second way.
Configurations below are listed in execution order, not grid order, with brackets around the part that should be looping. All start in r1c1.
Loops that crash (yay):
ZO MO CO PW RO SW (RO FL) ZO MO PW RO SW (RO FL) MO (FL RO PR) MO (CO RO PR) (variant of Caine's) ZO CO CO ZO (ZO PR) ZO ZO MO (RO PW FL ZO) (n.b. last ZO is against wall. might also be looping back to the FL above it.)
"Loops" that don't (boo):
ZO MO (RO PW FL ZO) (last ZO not against wall.) MO (FL RO ZO) (non-crashing variant of Caine's)
Discoveries
Here are the various configurations and logs that have been discovered.
General: Approaching the Master
Configuration
- Grid: zone mount run rotate rotate / -- -- popen rotate cache
- Command Path: zone, mount, popen, rotate, rotate, rotate, cache
Alternate Configuration
- Grid: zone mount run pwrite cache / -- -- popen rotate --
- Command Path: zone, mount, popen, rotate, pwrite, cache
Alternate Configuration
- Grid: zone mount run cache -- / -- -- rotate -- --
- Command Path: zone, mount, rotate, cache
Output
- Text:
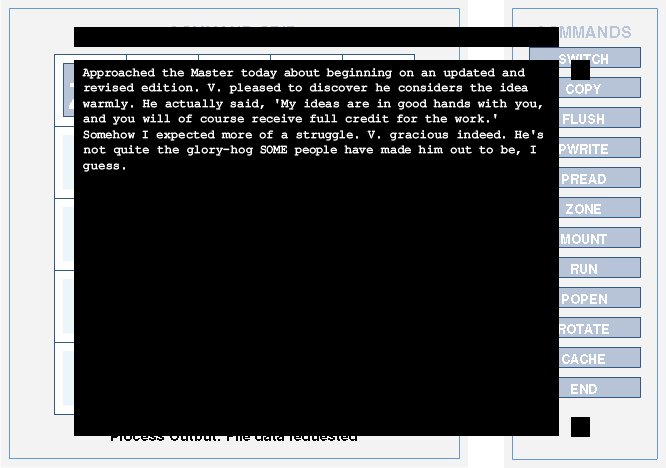
Approached the Master today about begining on an updated and revised edition. V. pleased to discover he considers the idea warmly. He actually said, 'My ideas are in good hands with you, and you will of course receive full credit for the work.' Somehow I expected more of a struggle. V. gracious indeed. He's not quite the glory-hog SOME people have made him out to be, I guess.
the Master probably refers to Sente
- Image:
General: Coffee
Configuration
- Grid: zone mount run switch -- / -- -- pwrite rotate flush / -- -- -- cache zone
- Command Path: zone, mount, pwrite, rotate, switch, flush, zone, cache
Output
- Text:
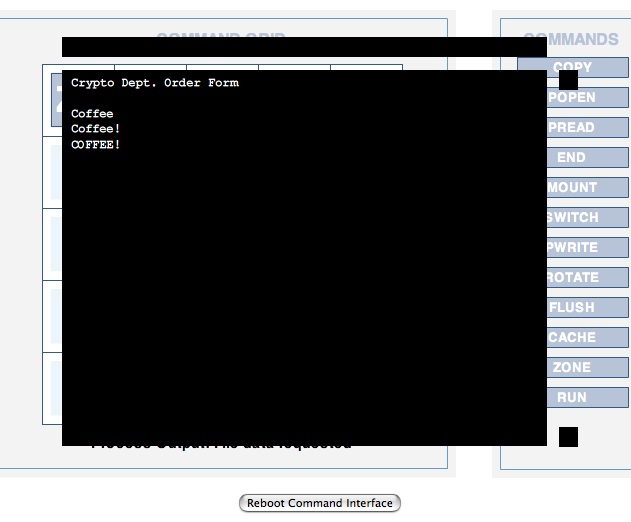
Crypto Dept. Order Form Coffee Coffee! COFFEE!
- Image:
General: Project Data
Configuration
- Grid: zone mount -- -- -- / -- switch pread -- -- / -- -- switch -- -- / -- -- -- switch cache / -- -- -- -- rotate
- Command Path: zone, mount, pread, switch, switch, switch, rotate, cache
Output
- Text:
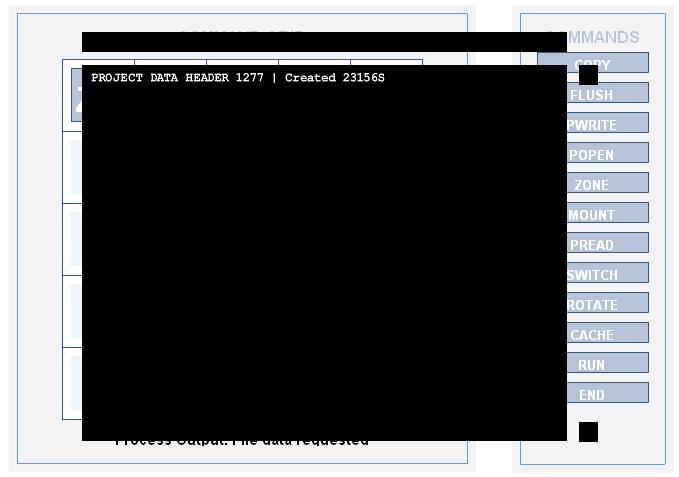
PROJECT DATA HEADER 1277 | Created 23156S
- Image:
General: Kiteway disrupting the department
Configuration
- Grid: zone mount -- -- -- / -- switch pread -- -- / -- -- switch cache -- / -- -- -- rotate --
- Command Path: zone, mount, pread, switch, swtich, rotate, cache
Alternate Configuration
- Grid: zone mount switch -- -- / run rotate copy switch cache / -- rotate pread -- rotate
- Command Path: zone, mount, copy, pread, rotate, rotate, switch, switch, rotate, cache
Output
- Text:
To: 55321801 FROM: MANSOOR H. Kiteway's programs are disrupting the entire department. Breeding hostility and distrust among amicable colleagues. The man doesn't belong here anymore, why can't he keep his damned pet projects in his own office? Crypto is mine now, not his. Well, here are the metrics to show he's not minding his own business. Number of times Kiteway has visited dept. offices this year: 78 And in 268: 129 And in 267: 23 Dept. suspicion level on the Howe-Panntonin Index: 8.8 And in 268: 7.3 And in 267: 4.5 Suspect the man has his own agenda and isn't sharing with the proper channels, for example me and you. Suspect he is subverting the time and resources of my faculty without consulting me ahead of time. Behaving as though he can't trust his own senior fellows. Ridiculous. How long must we put up with this childish rigmarole?
MANSOOR H. probably refers to Hunan Mansoor
Kiteway probably refers to Sente Kiteway
General: Big Nothing
Configuration
- Grid: zone mount -- -- -- / switch zone zone switch -- / -- pwrite rotate cache pread
- Command Path: zone, mount, zone, zone, switch, pwrite, rotate, switch, pread, cache
Output
- Image:
General: Krsa algorithm
Configuration
- Grid: end end mount -- -- / -- -- cache copy -- / -- -- rotate zone --
- Command Path: end, end, mount, copy, zone, rotate, cache
Output
- Text:
Notes:
To make this more precise, let Krsa be an RSA generator with associated security
parameter k and let Keys be the set of all moduli N that have positive probability
to be outbut by Krsa. Let Hash be a family of functions whose key-space is Keys and
such that HashN : { 0, 1}
-> Z
n for every N e Keys. Let DS = (Krsa, Sign, VG) be the digital signature scheme whose
signing and verifying algorithms are as follows:
Algorithm Sign N,p,qp,d (M)
y <- Hashn (M)
x <- yd mod N
Return x
Algorithm VGn,e (M,x)
y <- Hashn (M)
y
<- xe mod N
If y=y
then return 1 else return 0
See Wikipedia for signing messages with RSA. Some formatting may have been lost if text is from a copy-and-paste, which may have resulted in the odd-looking "If y=y" (originally, say, "y=y")
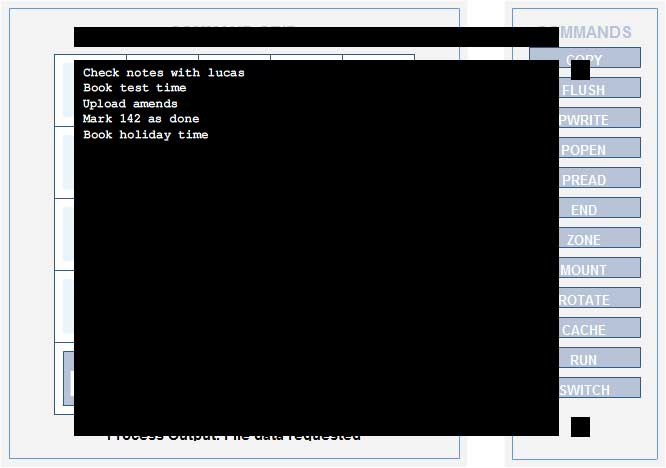
General: To-Do list
Configuration
- Grid: -- -- -- -- -- / -- -- -- -- -- / -- -- -- cache -- / -- -- mount rotate -- / end end zone rotate --
- Command Path: end, end, zone, mount, rotate, rotate, cache
- Times Found (UTC): 09:21 10-JUL-2005
Output
- Text:
Check notes with lucas Book test time Upload amends Mark 142 as done Book holiday time
lucas probably refers to Lucas Bazeries
- Image:
General: Drinks
Configuration
- Grid: end end mount -- -- / -- -- cache copy -- / -- -- rotate copy -- / -- -- rotate zone --
- Command Path: end, end, mount, copy, copy, zone, rotate, rotate, cache
- Times Found (UTC): 19:04
(N.B. I also get this output using config 22, at time of writing... -- Scribe)
Output
- Text:
From: TERM@830 To: TERM@620 Subject: drink? Date: 7 April 269 Are we on for a drink after work tonight? From: TERM@620 To: TERM@830 Subject: Re: drink? Date: 7 April 269 I don know - who else might be coming? From: TERM@830 To: TERM@620 Subject: Re: drink? Date: 7 April 269 Do you want other people to come? From: TERM@620 To: TERM@830 Subject: Re: drink? Date: 7 April 269 Of course. I a sociable creature. From: TERM@830 To: TERM@620 Subject: Re: drink? Date: 7 April 269 So Ie noticed. From: TERM@620 To: TERM@830 Subject: Re: drink? Date: 7 April 269 You should behave yourself. From: TERM@830 To: TERM@620 Subject: Re: drink? Date: 7 April 269 I am being the perfect gentleman, as always. From: TERM@620 To: TERM@830 Subject: Re: drink? Date: 7 April 269 Not sure about the perfect. Or the gentleman. ;-) From: TERM@830 To: TERM@620 Subject: Re: drink? Date: 7 April 269 So - the drink question. Other guests tonight? From: TERM@620 To: TERM@830 Subject: Re: drink? Date: 7 April 269 I think it would be good to invite the whole gang out and see who comes along. It feels like ages since wee all got together. It would be nice. From: TERM@830 To: TERM@620 Subject: Re: drink? Date: 7 April 269 You sure? From: TERM@620 To: TERM@830 Subject: Re: drink? Date: 7 April 269 Yes, I am.
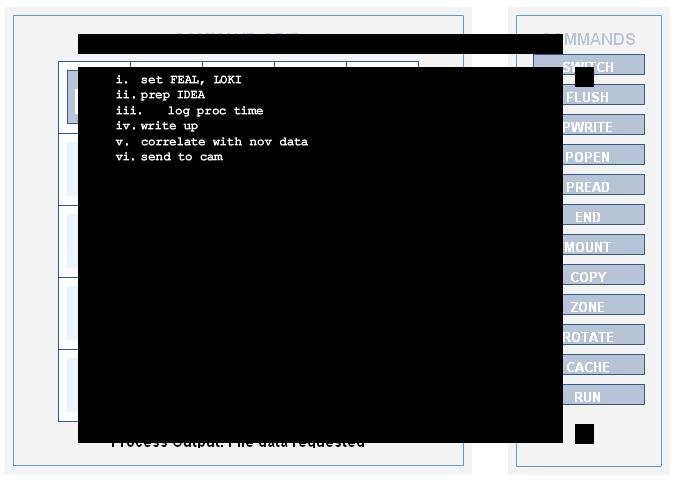
General: Alternate To-Do list
Configuration
- Grid: end end mount -- -- / -- -- cache copy -- / -- -- rotate zone --
- Command Path: end, end, mount, copy, zone, rotate, cache
- Times found (UTC): 22:02:40
Output
- Text:
i. set FEAL, LOKI ii.prep IDEA iii. log proc time iv.write up v. correlate with nov data vi.send to cam
- Image:
FEAL, LOKI and IDEA are all block cipher encryption algorithms. "Cam" is probably Camden Porta.
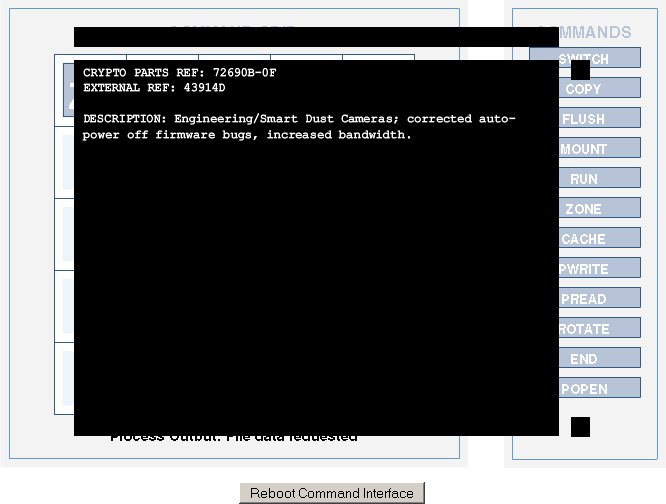
Part: Smart Dust Cameras (ref: 72690B-0F)
Configuration
- Grid: zone mount run rotate rotate / -- -- popen, zone, cache
- Command path: zone, mount, popen, zone, rotate, rotate, cache
Alternate Configuration
- Grid: zone mount -- rotate rotate / run -- copy rotate rotate / -- -- rotate cache zone
- Command Path: zone, mount, copy, rotate, rotate, rotate, rotate, rotate, zone, cache
Output
- Text:
CRYPTO PARTS REF: 72690B-0F
EXTERNAL REF: 43914D
DESCRIPTION: Engineering/Smart Dust Cameras; corrected auto-power off firmware bugs, increased bandwidth.
- Image:
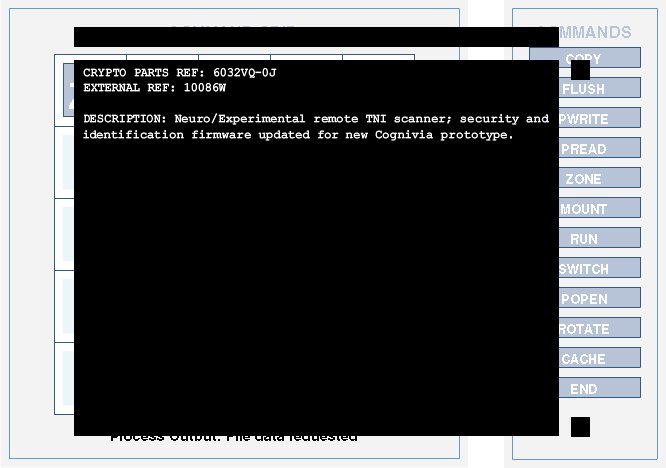
Part: Experimental remote TNI scanner (ref: 6032VQ-0J)
Configuration
- Grid: zone mount run switch -- / -- -- popen rotate cache
- Command Path: zone, mount, popen, rotate, switch, cache
Alternate Configuration
- Grid: zone mount run -- -- / -- -- switch cache -- / -- -- -- rotate --
- Command Path: zone, mount, switch, rotate, cache
Alternate Configuration
- Grid: zone mount run -- -- / -- -- mount -- -- / -- -- -- switch cache / -- -- -- -- rotate
- Command Path: zone, mount, mount, switch, rotate, cache
Output
- Text:
CRYPTO PARTS REF: 6032VQ-0J
EXTERNAL REF: 10086W
DESCRIPTION: Neuro/Experimental remote TNI scanner; security and identification firmware updated for new Cognivia prototype.
- Image:
Part: High Power phase-conjugate laser (ref: 384621-5A)
Configuration
- Grid: zone mount run -- –- / copy zone zone cache -- / copy pwrite rotate -- -- / copy rotate -- -- -- / rotate -- -- -- --
- Command Path: zone, mount, zone, zone, copy, copy, copy, rotate, rotate, pwrite, rotate, cache
Output
- Text:
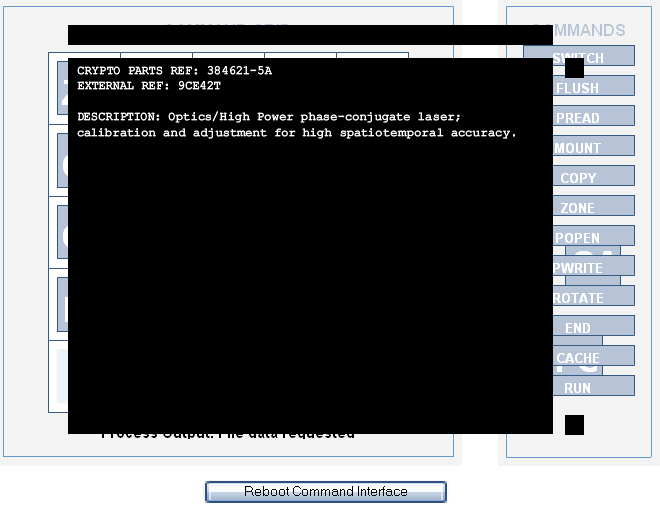
CRYPTO PARTS REF: 384621-5A
EXTERNAL REF: 9CE42T
DESCRIPTION: Optics/High Power phase-conjugate laser; calibration and adjustment for high spaciotemporal accuracy.
Image:
Part: Baker Spherical Magnetic Containment field (ref: 3141PU-1M)
Configuration
- Grid: zone mount run -- -- / copy zone zone cache -- / copy pwrite rotate -- -- / copy rotate -- -- -- / switch -- -- -- --
- Command Path: zone, mount, zone, zone, copy, copy, copy, switch, rotate, pwrite, rotate, cache
Output
- Text:
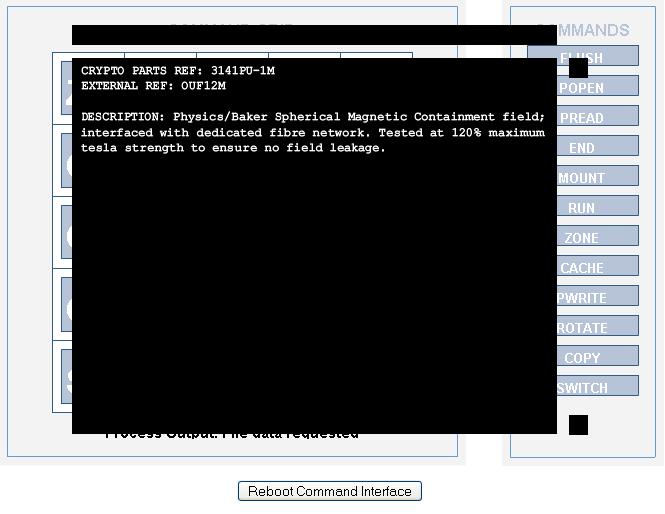
CRYPTO PARTS REF: 3141PU-1M
EXTERNAL REF: OUF12M
DESCRIPTION: Physics/Baker Spherical Magnetic Containment field; interfaced with dedicated fibre network. Tested at 120% maximum tesla strength to ensure no field leakage.
- Image:
Part: Nanoscale imager (ref: 62999E-3M)
Configuration
- Grid: zone mount -- -- -- / -- switch pread -- -- / -- -- switch -- cache / -- -- -- switch rotate / -- -- -- -- rotate
- Command Path: zone, mount, pread, switch, switch, switch, rotate, rotate, cache
Output
- Text:
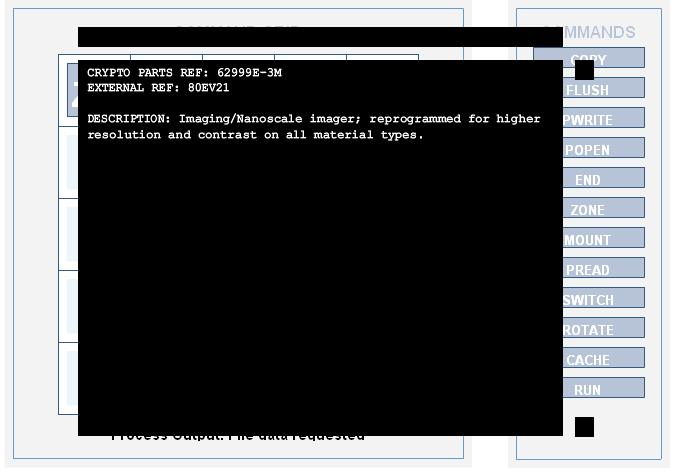
CRYPTO PARTS REF: 62999E-3M
EXTERNAL REF: 80EV21
DESCRIPTION: Imaging/Nanoscale imager; reprogrammed for higher resolution and contrast on all material types.
- Image:
Part: Reynolds ioniser (ref: 813QE2-7X)
Configuration
- Grid: zone mount -- -- -- / switch pread pread -- -- / -- switch -- -- -- / -- -- switch switch cache / -- -- -- rotate rotate
- Command Path: zone, mount, pread, pread, switch, switch, switch, rotate, switch, rotate, cache
Output
- Text:
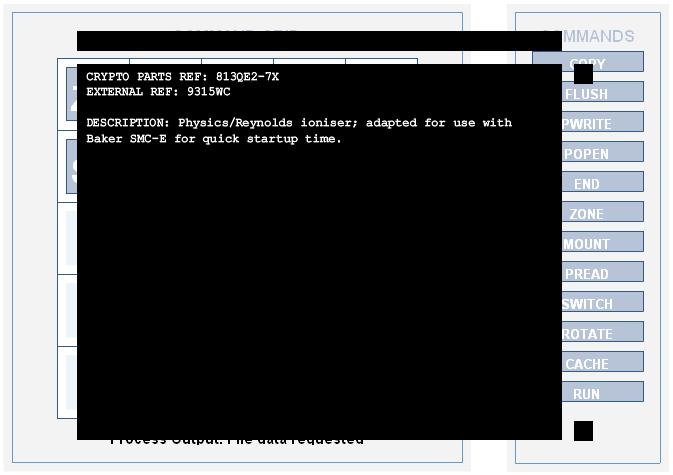
CRYPTO PARTS REF: 813QE2-7X
EXTERNAL REF: 9315WC
DESCRIPTION: Physics/Reynolds ioniser; adapted for use with Baker SMC-E for quick startup time.
- Image:
Part: Active Noise Control system (ref: 477DI5-2Y)
Configuration
- Grid: zone mount -- -- -- / -- copy zone switch -- / -- pwrite switch rotate cache / -- -- -- rotate --
- Command Path: zone, mount, zone, copy, pwrite, switch, rotate, rotate, switch, cache
Output
- Text:
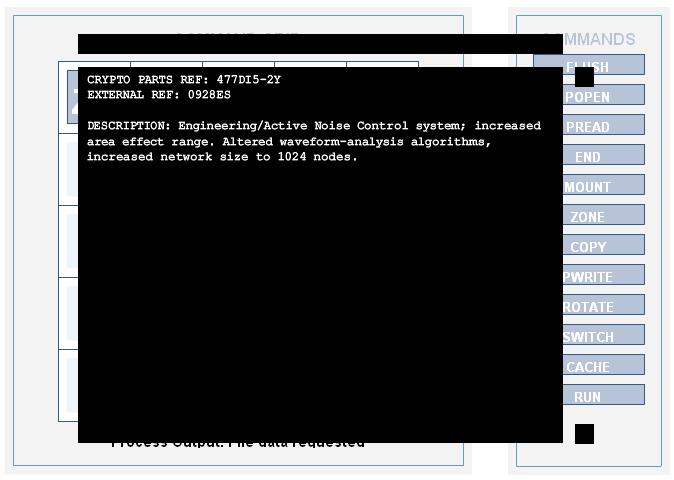
CRYPTO PARTS REF: 477DI5-2Y
EXTERNAL REF: 0928ES
DESCRIPTION: Engineering/Active Noise Control system; increased area effect range. Altered waveform-analysis algorithms, increased network size to 1024 nodes.
- Image:
Part: Yorke-Takayuki simulator (ref: 5239JL-4M)
Configuration
- Grid: zone mount -- -- -- / copy pread pread -- -- / copy switch -- -- -- / pwrite rotate switch cache -- / -- -- -- rotate --
- Command Path: zone, mount, pread, pread, copy, copy, pwrite, rotate, switch, switch, rotate, cache
Output
- Text:
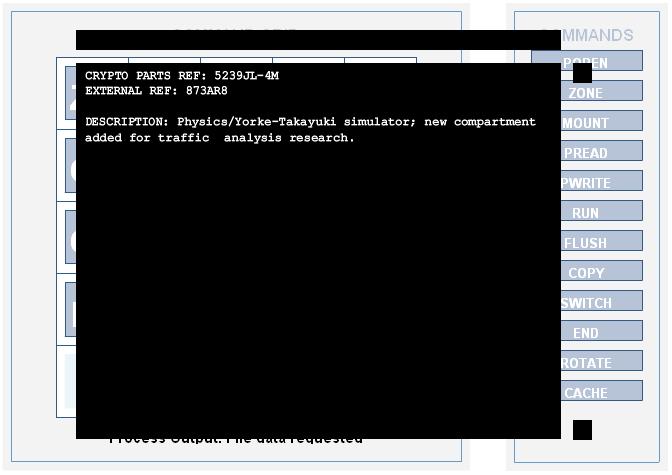
CRYPTO PARTS REF: 5239JL-4M
EXTERNAL REF: 873AR8
DESCRIPTION: Physics/Yorke-Takayuki simulator; new compartment added for traffic analysis research.
- Image:
Part: Quadropole Magnet Current Regulators (ref: 5BPK76-8H)
Configuration
- Grid: zone mount -- -- -- / switch zone zone -- -- / -- switch -- -- -- / -- -- switch switch cache / -- -- -- rotate rotate
Command Path: zone, mount, zone, zone, switch, switch, switch, rotate, switch, rotate, cache
Output
- Text:
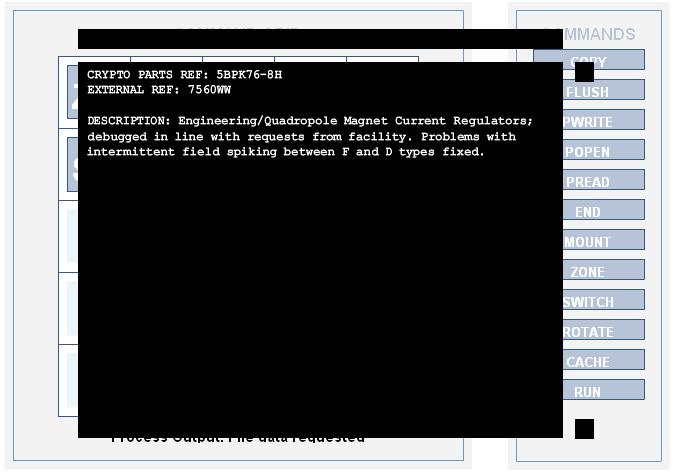
CRYPTO PARTS REF: 5BPK76-8H
EXTERNAL REF: 7560WW
DESCRIPTION: Engineering/Quadropole Magnet Current Regulators; debugged in line with requests from facility. Problems with intermittent field spiking between F and D types fixed.
- Image:
Part: 174-Ytterbium Atomic Clock (ref: 254ID9-3R)
Configuration
- Grid: zone mount -- -- -- / switch zone zone -- -- / -- switch -- -- -- / -- -- switch cache -- / -- -- -- rotate --
- Command Path: zone, mount, zone, zone, switch, switch, switch, rotate, cache
Output
- Text:
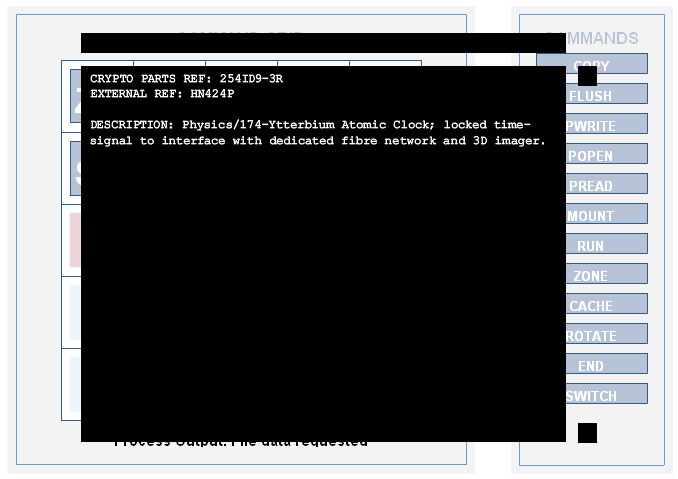
CRYPTO PARTS REF: 254ID9-3R
EXTERNAL REF: HN424P
DESCRIPTION: Physics/174-Ytterbium Atomic Clock; locked time-signal to interface with dedicated fibre network and 3D imager.
- Image:
Part: Broadman Nuclear decay RNG (ref: 3085NC-6R)
Configuration
- Grid: zone mount -- -- -- / zone zone zone -- -- / pwrite rotate switch -- -- / -- -- -- cache --
- Command Path: zone, mount, zone, zone, zone, pwrite, rotate, switch, cache
Output
- Text:
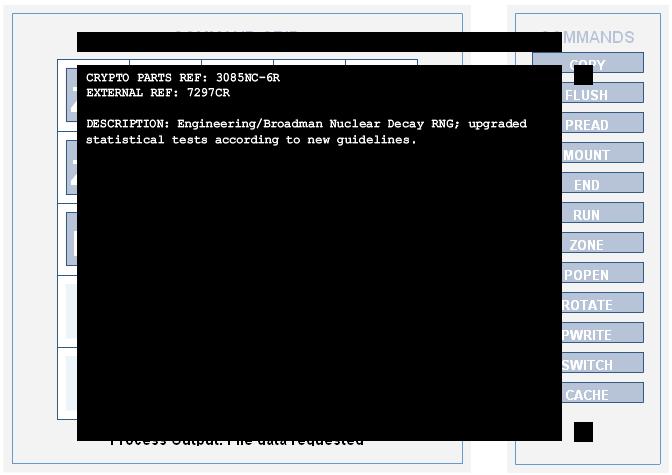
CRYPTO PARTS REF: 3085NC-6R
EXTERNAL REF: 7297CR
DESCRIPTION: Engineering/Broadman Nuclear Decay RNG; upgraded statistical tests according to new guidelines.
- Image:
Part: WHISK array (ref: 177ETC-1U)
Configuration
- Grid: zone mount -- -- -- / -- -- switch -- -- / cache -- -- switch -- / rotate pread zone zone zone
- Command Path: zone, mount, switch, switch, zone, zone, zone, pread, cache
Output
- Text:
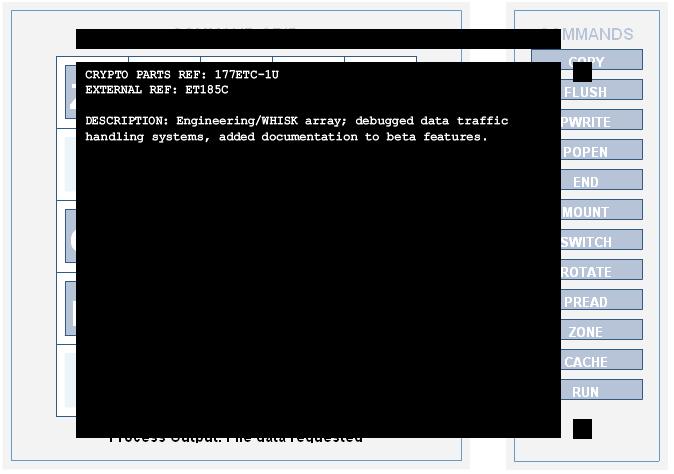
CRYPTO PARTS REF: 177ETC-1U
EXTERNAL REF: ET185C
DESCRIPTION: Engineering/WHISK array; debugged data traffic handling systems, added documentation to beta features.
- Image:
Part: Tajison Plasma Wakefield Accelerator (ref: 9451RZ-4U)
Configuration
- Grid: zone mount -- -- -- / -- switch zone -- --/ -- -- switch -- cache / -- -- -- switch rotate / -- -- -- rotate switch
- Command Path: zone, mount, zone, switch, switch, switch, switch, rotate, rotate, cache
Output
- Text:
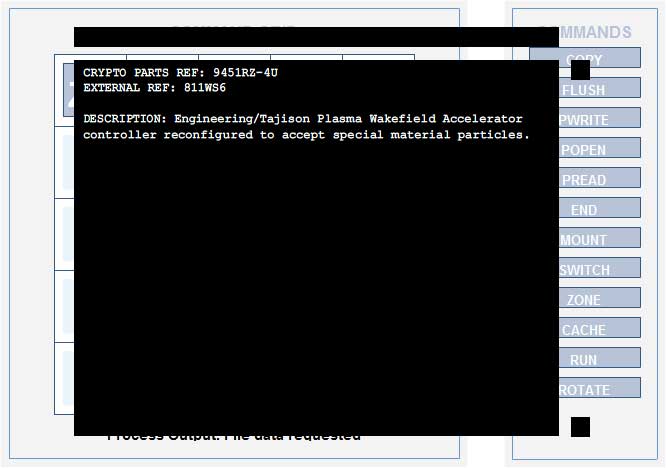
CRYPTO PARTS REF: 9451RZ-4U
EXTERNAL REF: 811WS6
DESCRIPTION: Engineering/Tajison Plasma Wakefield Accelerator controller reconfigured to accept special material particles.
- Image:
Part: Nelis Nuclear Isomer Battery (Hf-178-2m) (ref: 26637C-8Y)
Configuration
- Grid: zone mount -- -- -- / -- switch zone -- cache / -- -- switch -- rotate / -- -- -- switch rotate / -- -- -- rotate switch
- Command Path: zone, mount, zone, switch, switch, switch, switch, rotate, rotate, rotate, cache
Output
- Text:
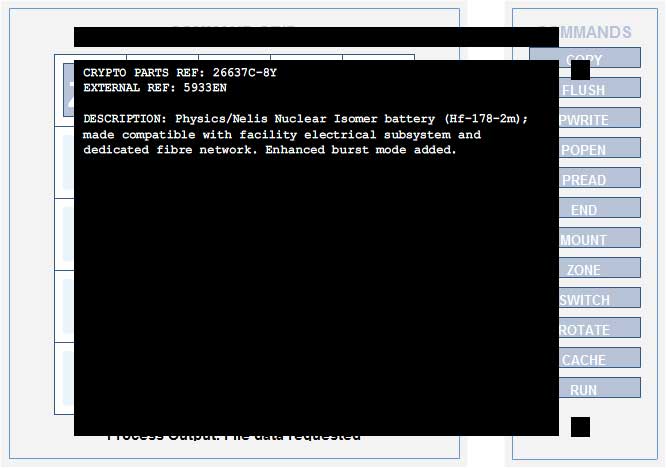
CRYPTO PARTS REF: 26637C-8Y
EXTERNAL REF: 5933EN
DESCRIPTION: Physics/Nelis Nuclear Isomer battery (Hf-178-2m); made compatible with facility electrical subsystem and dedicated fibre network. Enhanced burst mode added.
- Image:
Part: Klebold plates (ref: 122C76-3S)
Configuration
- Grid: mount zone rotate switch -- / -- rotate -- -- popen / -- -- switch zone zone / -- -- -- switch -- / -- -- cache pread zone
- Command Path: mount, rotate, zone, rotate, switch, popen, zone, zone, switch, switch, zone, pread, cache
Output
- Text:
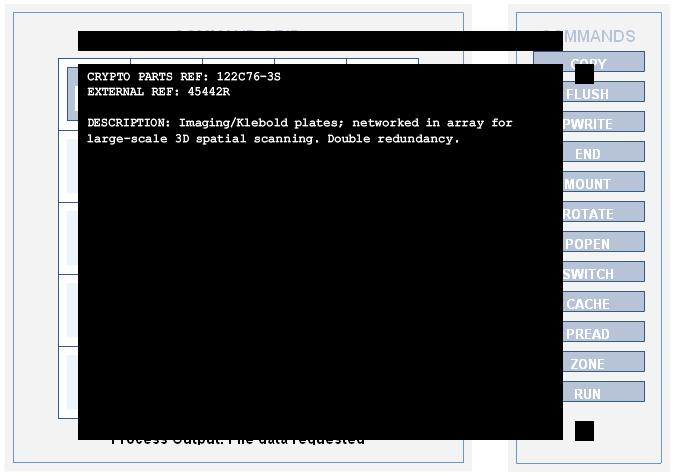
CRYPTO PARTS REF: 122C76-3S
EXTERNAL REF: 45442R
DESCRIPTION: Imaging/Klebold plates; networked in array for large-scale 3D spatial scanning. Double redundancy.
- Image:
Part: Flux Compression Generator (ref: 460WDN-4X)
Configuration
- Grid: zone mount rotate switch -- / -- -- rotate -- popen / -- -- switch zone zone / -- -- -- switch -- / -- -- cache pread zone
- Command Path: zone, mount, rotate, rotate, switch, popen, zone, zone, switch, switch, zone, pread, cache
Output
- Text:
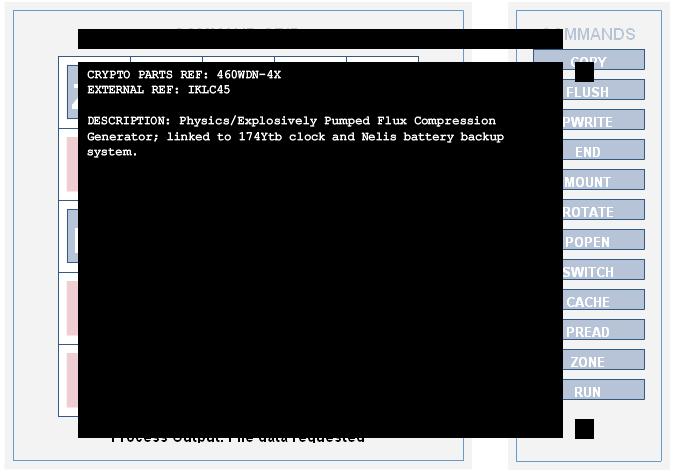
CRYPTO PARTS REF: 460WDN-4X
EXTERNAL REF: IKLC45
DESCRIPTION: Physics/Explosively Pumped Flux Compression Generator; linked to 174Ytb clock and Nelis battery backup system.
- Image:
Logs: Gatehouse 24
When this configuration is run, a message Operation in progress appears. The screen then distorts and wavers. Finally, a log appears. Discussion on Unforums suggests that the logs may rotate, or appear randomly.
Configuration
- Grid: zone mount run -- -- / -- -- copy switch flush / -- -- pwrite rotate rotate
- Command Path: zone, mount, copy, pwrite, rotate, switch, rotate, flush
Alternate Configuration
- Grid: zone mount run switch flush / -- -- pwrite rotate rotate
- Command Path: zone, mount, pwrite, rotate, switch, rotate, flush
Output 1
[ GATEHOUSE 24 ]
:: start 143805 +000000
:: start 143805 +000000
:: archive location { dev 7 }
:: index { yes }
:: retention { 9 }
:: processing time { 0.53 }
::
A
// labeled A;
// triangulated location mapped;
// passive badge { present }
// badge query { friedberg, i {119yr} }
You really said that [?]
// preliminary review complete
B
// labeled B;
// triangulated location mapped;
// passive badge { present }
// badge query { carrick, h {624yr} }
I was hungry [!] I'm not diplomatic when I'm starving [.]
// preliminary review complete
// 45% positive emotional state
// cross reference surveillance footage
{ extrapolated: badge {line 16} extracted }
{ gatekeeper system 24;
active badge interrogated, passed }
FRIEDBERG, I
I bet you fifty lecks your stuff is wiped when you get back [.]
// preliminary review complete
CARRICK, H
Hah [,] I'd like to see him even try [.]
// preliminary review complete
[ LOG EXCERPT ENDS ]
Output 2
[ GATEHOUSE 24 ]
:: start 055814 +000000
:: start 061055 +000000
:: archive location { dev 7 }
:: index { yes }
:: retention { 9 }
:: processing time { 0.53 }
::
A
// labeled A;
// triangulated location mapped;
// passive badge { present }
// badge query { porta, c {112yr} }
Where have you been [?]
// preliminary review complete
B
// labeled B;
// triangulated location mapped;
// passive badge { present }
// badge query { bazeries, l {520yr} }
So I'm a little late [.] Relax [.]
// preliminary review complete
// 45% positive emotional state
// cross reference surveillance footage
{ extrapolated: badge {line 16} extracted }
{ gatekeeper system 24;
active badge interrogated, passed }
PORTA, C
We have to hurry and get this thing done [.]
// preliminary review complete
BAZERIES, L
Is he here yet [?]
// preliminary review complete
PORTA, C
I think so [.] Let's hurry [.]
// preliminary review complete
BAZERIES, L
I hope there's coffee [.]
// preliminary review complete
PORTA, C
Focus on the project [,] dunderhead [.]
// preliminary review complete
[ LOG EXCERPT ENDS ]
Output 3
[ GATEHOUSE 24 ]
:: start 192355 +000000
:: start 192401 +000000
:: archive location { dev 7 }
:: index { yes }
:: retention { 9 }
:: processing time { 0.53 }
::
A
// labeled A;
// triangulated location mapped;
// passive badge { present }
// badge query { ashford, r {737yr} }
Hey [,] wait up [.]
// preliminary review complete
B
// labeled B;
// triangulated location mapped;
// passive badge { present }
// badge query { wooster, m {019yr} }
Oh [,] sorry [.] Hard meeting today [.]
// preliminary review complete
// 23% positive emotional state
// cross reference surveillance footage
{ extrapolated: badge {line 16} extracted }
{ gatekeeper system 24;
active badge interrogated, passed }
ASHFORD, R
Do you ever wonder [...]
// preliminary review complete
WOOSTER, M
Don't say it [.]
// preliminary review complete
ASHFORD, R
I know [,] I know [.] No place is safe [.]
// preliminary review complete
[ LOG EXCERPT ENDS ]
Audio: 14th of July 2005
Configuration
- Grid: end end mount rotate rotate / -- cache -- rotate rotate / -- rotate pread zone zone
- Command Path: end, end, mount, rotate, rotate, rotate, rotate, zone, zone, pread, rotate, cache
- Times found (UTC): 16:52:09, 17:19:23
Output
- Audio: MP3 file
- Estimated Recording Date: 14-JUL-05
- Transcription:
So you've got what you wanted.
It's Thursday the, what ... 14th of July? And here's your report.
I don't know what you're expecting to hear but ... I don't know what's going on; it might be nothing. I ... I could be getting completely paranoid as well. I mean with you lot snooping round I'm already on eggshells.
<swallow> Camden keeps watching me across the office - pretty sure he doesn't trust me.
I might be imagining it all I .. I dunno. Anyway, today I think I saw something odd. And it - and it might not be anything but if it keeps you happy here it is.
We got this delivery - we get deliveries all the time, you know hardware upgrades and stuff, but there was an extra item. It wasn't on the manifest. I only noticed it cos I was nearest the door when it all arrived, so I ended up signing for it.
So there was ... there was this packing case and, now I don't know what's in there. And it's locked in the stores now so I ... I can't get to it even if you want me to - it's about 5 feet high, 3 feet across and quite slim, like ... a painting or something.
So is this an art-theft thing? Is that what you're after - some kind of fence operation? And if you told me what to look for I might have a better chance of helping.
<tsk> Well - that's it. I'll ... I'll let you know if anything else happens.
- Image:
Audio: Packing case gone
Configuration
- Grid: end end mount -- -- / -- -- cache copy -- / -- -- rotate copy -- / -- -- rotate zone --
- Command Path: end, end, mount, copy, copy, zone, rotate, rotate, cache
- Times found (UTC): 22:02:40 (22-24 [?])
Output
- Audio: MP3 file
- Estimated Recording Date: July 25th based on her date with Kurt which we know was on July 26th
- Transcription:
Well, hello again.
<sigh> I hate talking into these things. Hang on, I think someone's coming! <rustly noises> No, no, it's alright.
Right, okay... that packing case... it's disappeared.
I don't know when it went, but it's not there today. So I.. I think I saw it a couple of days ago... that was the last time. Not much help, I know.
I gave the case a bit of a kick the other day, to see if I could hear what was in there. I think it was tech stuff.
Anyway, I'm meeting up with a guy for lunch tomorrow, and he's kind of a hardware freak. So I might try kind of nudging him, see if there's anything going on. He's a nice guy, so he might be helpful.
I'm not going to do anything, y'know, just to get information for you. It's bad enough sneaking around like this. I can't just talk to people anymore, it's like I'm always interrogating them, even my friends. I can't look at anything without suspecting it. It'll do my head in.
<sigh> You'd better look after your side of the bargain. It's the only reason i'm doing this.
Audio: Encryption themes
Configuration
- Grid: end end mount -- -- / -- -- cache copy -- / -- -- rotate zone --
- Command Path: end, end, mount, copy, zone, rotate, cache
- Times found (UTC): 19:20:54, 19:58:48, 20:02:01, 20:13:45, 20:30:37, 20:57:23, 21:01:26, 21:26:08
Output
- Audio: MP3 file
- Transcription:
I saw my dad the other day so, thanks, he told me about everything and... Well I’m, I’m just glad there’s a point to all this; he’s... he’s looking much better... and I suppose that means that you’re happy with how I’m doing, so I’m... probably on the right track?
I’ve been keeping an eye on the deliveries here, um I don’t think there has been anything funny for weeks now, but , you’know, I might have missed something. There have been a couple of odd projects coming across my desk though. Nobody ever gets the full picture here, but I’ve noticed some themes in the encryption work I’m doing, for a start it’s pretty advanced, everything’s been marked for ‘quantum’ (which isn’t perfect yet, but it’s about the highest level we’ve got). But <sigh> there are a couple of words that keep coming up too and... well, I <stumbles over words> I don’t have a clear picture of what they mean, but maybe they’ll mean something to you, the sender or the recipient is always called ‘Viendenbourg’ and there are all these references to ‘the material’ and how much of it they’ve got. I know I’m not seeing all the messages, they spread the work around – you’know, security - but only a few of us can handle quantum encryption so I’m seeing a fair chunk of the correspondence. It just seems odd it needs to be so secret, so... that’s why I mention it.
I’d better go soon, there’s umm, a protest outside the museum and it will take me ages to get past them. Anyway... I can’t think of anything else... nope that’s it.
Audio: Suspicious delivery guy
Configuration
- Grid: end end zone mount -- / -- -- -- -- copy / -- -- -- -- rotate / -- -- -- -- rotate / -- -- -- -- cache
- Command Path: end, end, zone, mount, copy, rotate, rotate, cache
Output
- Audio: MP3 file
- Estimated Recording Date: Shortly after 03-JAN-06 (link)
- Transcription:
If he dies, you realise that's it. You can do what you like to me - I don't care about me.
Someone in my block got beaten up the other night. He isn't a violent guy; he's a calligrapher. But he just got attacked well f ... nothing basically. Well I think it was random, but I don't think I believe in random any more. Was it you?
Are you trying to scare me? You don't need to so just ... stop it.
I did what you wanted anyway. Last night ...
I worked until I was the only one left in the office. Must have been about 11 when this delivery guy turned up with a trolley full of boxes. And he did look a bit surprised to see me there. These two big boxes were for us, so I signed for them and went next door to grab Angelica so she could open the stores.
Anyway, the boxes were really heavy, so the delivery guy wheeled the trolley into the stores and dropped them off there. Then I saw him slide one of our cases under the trolley; when he moved the trolley, it wasn't there anymore. It was quick but I'm sure he swiped something. Then he left, and Angelica locked the door.
I would have followed him ... well, probably ... but Angelica started talking to me about my research and I couldn't just rush off. I saw him go to the end of the corridor ... to the elevator, and he hit the down button. There's only the basement under us, but I think there might be passageways for internal mail and things. I honestly don't know. And I'm not going down there in the middle of the night, so don't ask. No matter what you threaten me with.
Ummm the delivery guy was about 6 foot, white, short dark hair. I haven't seen him before.
Keep an eye out, will you?
- Image:
Audio: Over and out
Configuration
- Grid: end end zone mount cache / -- -- -- -- rotate
- Command Path: end, end, zone, mount, rotate, cache
- Times Found (UTC): 09:23 10-JUL-2006
Output
- Audio: MP3 file
- Estimated Recording Date: Shortly after 19-JAN-06? (link) Maybe February, judging from "since January" in text. Probably the last in the series.
- Transcription:
So this is it. Can't say I'm not glad it's over but, well, one day maybe you can tell me what this was all about. I mean, I read the papers - police raids on subway stations - sounds like your kind of thing.
We've had a few more deliveries come in since January, but still no sign of the mystery man. It's been a different courier each time, and they've - they've all looked pretty innocent. The Viendenbourg messages are still going backwards and forwards.
I appreciate what you've done for my dad, but ... I've done my bit. That's it. That was the deal. You can go digging around in the tunnels if you like but don't expect me to do any more of your dirty work. You told me to stop, so I'm stopping.
Don't ever tell my dad about this.
Over and out.
- Image:
Audio: Getting dodgy
Configuration
- Grid: end end mount -- -- / -- -- cache copy -- / -- -- rotate zone --
- Command Path: end, end, mount, copy, zone, rotate, cache
Output
- Audio: MP3 file
- Estimated Recording Date: ?? But before the previous message. Summer solstice shutdown is in June, so perhaps JUN-05? (link)
- Transcription:
Look this is getting seriously dodgy.
Last week, Lucas completely cut me out of a meeting, and Mansoor has been ripping into my white paper and...
I'm sure it's not professional, it's personal. They know what we're up to, I swear. No I don't, I don't know anything. I'm losing it. Please, I can't be that important. You could get someone else.
The whole place is shutting down over Solstice. You...you could get someone to break in here and I don't know...isotope tag one of the packages and track it you probably do that all the time...what do you need me for?
Well, happy holidays.
- Image:
Historical Cryptographers
Some of the names mentioned in the logs share the names of historic cryptographers and mathematicians.
- Bazeries
- French military cryptographer, the 'pragmatic man of cryptology'. Famous for breaking the French 'Great Cipher' created in the 17th century.
- Porta
- Giovanni Battista Porta, Italian cryptographer and inventor of the Della Porta cipher - a polyalphabetic cipher with keyword.
- Ashford
- the name of the village in Kent where John Wallis, 17th century mathematician, was born. He wrote among other things, about the quadrature of curves, logic, theology and cryptography.
- Carrick
- the name of a Windows-based encryption application, designed by cryptographer Bruce Schneier.