The Thirteenth Labour: Difference between revisions
No edit summary |
No edit summary |
||
| (9 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
==Card | {{Season1}} | ||
''The Thirteenth Labour'' is a puzzle card from the first season of Perplex City, challenging players to brute-force an encryption using distributed computing. | |||
It was solved in 2010 by forum user paraboloid13, who posted the decrypted message to the We Love Puzzles forum in February 2010.<ref name="paraboloid WLP 1">[https://web.archive.org/web/20100227084832/http://www.welovepuzzles.com/jforum/posts/list/15/343.page We Love Puzzles forum archive page]</ref> They provided some hints but did not explain how they solved the puzzle. | |||
This was the second-to-last solvable Perplex City card, followed by [[Billion to One]], which was solved in 2020. The only remaining card is [[Riemann]]. | |||
[https://perplexcitycardcatalog.com/1/251/ Perplex City Card Catalog: Season 1 Card #251 - The Thirteenth Labour] | |||
=={{Card|251|The Thirteenth Labour}}== | |||
[[Image:Thirteenthlabour.JPG]] | [[Image:Thirteenthlabour.JPG]] | ||
| Line 7: | Line 17: | ||
{| border="0" cellpadding="10" style="border: 2px solid #ddddff;" bgcolor="#f3f3ff" | {| border="0" cellpadding="10" style="border: 2px solid #ddddff;" bgcolor="#f3f3ff" | ||
| | | | ||
64/12/8 | 64/12/8 | ||
69 A9 3A FD C5 AD 43 8F 48 53 56 0F | 69 A9 3A FD C5 AD 43 8F 48 53 56 0F | ||
| Line 39: | Line 49: | ||
BF EC 20 11 70 71 AA 22 | BF EC 20 11 70 71 AA 22 | ||
[[Image:Cowhead.gif]] [[Image:Cowhead.gif]] [[Image:Cowhead.gif]] [[Image:Cowhead.gif]] [[Image:Cowhead.gif]] | [[Image:Cowhead.gif]] [[Image:Cowhead.gif]] [[Image:Cowhead.gif]] [[Image:Cowhead.gif]] [[Image:Cowhead.gif]] | ||
|} | |} | ||
==Puzzle solution== | |||
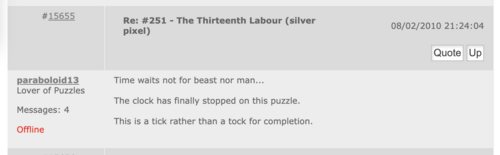
On February 8, 2010, We Love Puzzles forum user paraboloid13 posted the text of the decrypted message.<ref name="paraboloid WLP 1">[https://web.archive.org/web/20100227084832/http://www.welovepuzzles.com/jforum/posts/list/15/343.page We Love Puzzles forum archive page]</ref> | |||
<blockquote>Time waits not for beast nor man... | |||
The clock has finally stopped on this puzzle. | |||
This is a tick rather than a tock for completion.</blockquote> | |||
[[File:Parabaloid13-1.png|500px]] | |||
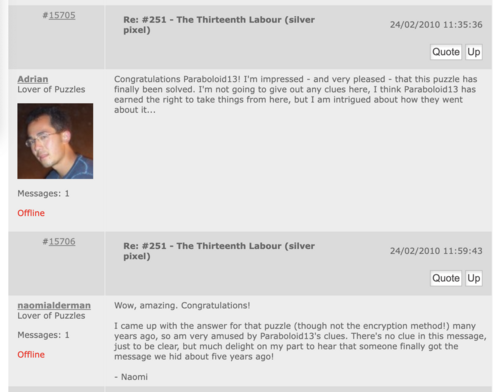
Adrian Hon and Naomi Alderman posted on the forum to confirm that the solution was correct<ref name="WLP Adrian and Naomi">[https://web.archive.org/web/20100227093430/http://www.welovepuzzles.com/jforum/posts/list/60/343.page We Love Puzzles - Adrian and Naomi posting]</ref>. | |||
[[File:Adriannaomi.png|500px]] | |||
==Parabaloid13's hints== | |||
User Parabaloid13 posted several hints about how they reached the solution but never shared a full explanation of their methodology. | |||
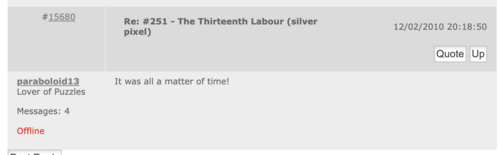
'''12 February 2010''' ([https://web.archive.org/web/20100227093310/http://www.welovepuzzles.com/jforum/posts/list/30/343.page Archive link]):<blockquote> | |||
It was all a matter of time!</blockquote> | |||
[[File:Parabaloid13-2.png|500px]] | |||
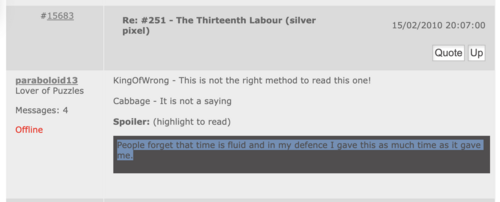
'''15 February 2010''' ([https://web.archive.org/web/20100227093425/http://www.welovepuzzles.com/jforum/posts/list/45/343.page Archive link]):<blockquote>KingOfWrong - This is not the right method to read this one! | |||
Cabbage - It is not a saying | |||
People forget that time is fluid and in my defence I gave this as much time as it gave me.</blockquote> | |||
[[File:Parabaloid13-3.png|500px]] | |||
'''18 February 2010''' ([https://web.archive.org/web/20100227093425/http://www.welovepuzzles.com/jforum/posts/list/45/343.page Archive link]): | |||
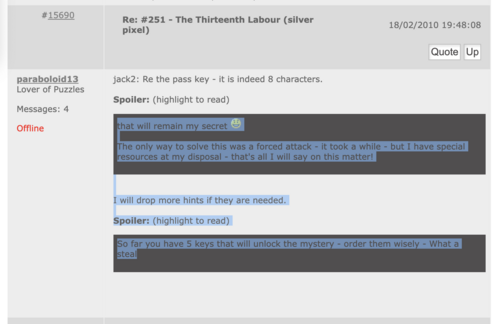
<blockquote>jack2: Re the pass key - it is indeed 8 characters. | |||
that will remain my secret | |||
The only way to solve this was a forced attack - it took a while - but I have special resources at my disposal - that's all I will say on this matter! | |||
I will drop more hints if they are needed. | |||
So far you have 5 keys that will unlock the mystery - order them wisely - What a steal</blockquote> | |||
[[File:Parabaloid13-4.png|500px]] | |||
==References== | |||
<references /> | |||
-- | |||
'''''The following text is the original content of this wiki page, discussing theories and methods. It is left here for archival purposes. It is unknown how user paraboloid13 solved the puzzle.''''' | |||
| Line 59: | Line 127: | ||
** Also, if this does need a brute force or grid computing attack - this would be a 'Herculean Challenge' | ** Also, if this does need a brute force or grid computing attack - this would be a 'Herculean Challenge' | ||
The distributed assault is currently underway, see below and at the [http://www.13thlabour.tk Assault on 13th Labour] site. | |||
==Cowheads and 64/12/8== | ==Cowheads and 64/12/8== | ||
| Line 71: | Line 140: | ||
==Distributed Effort== | ==Distributed Effort== | ||
Recently, work has been done by [[User:chimera245|chimera245]] to set up a coordinated Grid Computing solve on this Card. There is more information on this [http://www.13thlabour.tk here] kindly maintained by [[User:GuiN|GuiN]]. The Grid Client is running nicely and is available [http://www.e-wire.net.au/~eb_oakla/pxc/13labour_1_3_1.zip here]. | |||
Earlier efforts included some work by [[User:Scott|Scott]] who did some math, and observed how long it would take to work out an answer here. See: [[Rccrypt Work Unit checkout]] for the original proposal for a combined effort. | |||
Update: | |||
As of 23-SEP-06, the client has tried every single combination of letters and numbers. That is, every single 8 character combination of the characters: ''abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789''. Nothing has come of this. Basically, this means that the key to unlocking the code HAS to contain at least one symbol. [[User:chimera245|Chimera245]] has updated the program, adding 5 more characters to test - ''<space>'' ''.'' '','' ''?'' and ''!'' - This will double the size of the possible keyspace. | |||
{{CardCat}} | {{CardCat}} | ||
Latest revision as of 20:00, 3 March 2023
|
PERPLEX CITY, SEASON ONE |
The Thirteenth Labour is a puzzle card from the first season of Perplex City, challenging players to brute-force an encryption using distributed computing.
It was solved in 2010 by forum user paraboloid13, who posted the decrypted message to the We Love Puzzles forum in February 2010.[1] They provided some hints but did not explain how they solved the puzzle.
This was the second-to-last solvable Perplex City card, followed by Billion to One, which was solved in 2020. The only remaining card is Riemann.
Perplex City Card Catalog: Season 1 Card #251 - The Thirteenth Labour
Season 1 Card #251 - The Thirteenth Labour
Card text
Puzzle solution
On February 8, 2010, We Love Puzzles forum user paraboloid13 posted the text of the decrypted message.[1]
Time waits not for beast nor man...
The clock has finally stopped on this puzzle.
This is a tick rather than a tock for completion.
Adrian Hon and Naomi Alderman posted on the forum to confirm that the solution was correct[2].
Parabaloid13's hints
User Parabaloid13 posted several hints about how they reached the solution but never shared a full explanation of their methodology.
12 February 2010 (Archive link):
It was all a matter of time!
15 February 2010 (Archive link):
KingOfWrong - This is not the right method to read this one!
Cabbage - It is not a saying
People forget that time is fluid and in my defence I gave this as much time as it gave me.
18 February 2010 (Archive link):
jack2: Re the pass key - it is indeed 8 characters.
that will remain my secretThe only way to solve this was a forced attack - it took a while - but I have special resources at my disposal - that's all I will say on this matter!
I will drop more hints if they are needed.So far you have 5 keys that will unlock the mystery - order them wisely - What a steal
References
--
The following text is the original content of this wiki page, discussing theories and methods. It is left here for archival purposes. It is unknown how user paraboloid13 solved the puzzle.
The absolute basics
- We assume a block of text has been scrambled (encrypted) so that we cannot read it
- the RC5.64 standard refers to how it has been scrambled
- This scrambling requires a 'Key' to unlock it - we are searching for that key.
- So there are two camps
- one camp is supplying thousands of words randomly as keys to see if that produces anything reasonable
- The other camp is trying to figure out the appropriate word (perhaps using the Labours of Hercules as a clue) then trying that word
- http://www.connected.ltd.uk/pxc/
- Of course, if we are wrong about the encryption standard, then we are fairly fubarred, but it would appear that all roads point to it.
- Of course, there was some speculation that the 12 referred to the fact that there were 12 tasks of Hercules, and 12 RC5 challenges posted by RSA security
- This was therefore the '13th Challenge'
- Also, if this does need a brute force or grid computing attack - this would be a 'Herculean Challenge'
The distributed assault is currently underway, see below and at the Assault on 13th Labour site.
Cowheads and 64/12/8
- The cows represent the symbol of distributed.net, who first cracked the RC5.64 protocol, possibly indicating that this card requires a simple RC5.64 crack as well
- However, the card doesn't say RC5.64, it says 64/12/8. The assumption is that:
- the 5 cow heads is a pointer to the RC5 standards, as worked on by the folks at www.distributed.net
- The 64 would therefore be the encryption standard (RC5.64)
- The 12 is supposedly the number of rounds, and the key is 8 characters long
- That is why the brute force using 8 character words and phrases
Distributed Effort
Recently, work has been done by chimera245 to set up a coordinated Grid Computing solve on this Card. There is more information on this here kindly maintained by GuiN. The Grid Client is running nicely and is available here.
Earlier efforts included some work by Scott who did some math, and observed how long it would take to work out an answer here. See: Rccrypt Work Unit checkout for the original proposal for a combined effort.
Update:
As of 23-SEP-06, the client has tried every single combination of letters and numbers. That is, every single 8 character combination of the characters: abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789. Nothing has come of this. Basically, this means that the key to unlocking the code HAS to contain at least one symbol. Chimera245 has updated the program, adding 5 more characters to test - <space> . , ? and ! - This will double the size of the possible keyspace.

|
Please see Brian Enigma's impressive Card Catalog for a sorted, comprehensive listing of cards. |