Theft Case Notes/OB
From Perplex City Wiki
Jump to navigationJump to search
++++ PERSONAL CASE NOTES - OPERATION BAYONET ++++
Lead investigator: Detective Helena Frye
Notes: This is a dark project.
Objectives
* Objective 1: Locate, neutralise and detain the Third Power
* Objective 2: Rescue any civilians being held
* Objective 3: Retrieve any information related to the Receda Cube's location
Current Status
* Attacking Third Power encryption (negligible chance of success)
* Locating the destination of messages sent from Earth via the CRR and Relaynet
* Attempting to discover the method the Third Power are using to transmit message from their base back to the CRR, and then Earth
Relaynet Intercepts
Last week, Signals Intelligence members from the Perplex City Police confirmed that the Third Power was using Relaynet to send unauthorised messages to an unknown location. While much is still unclear, the following is known:
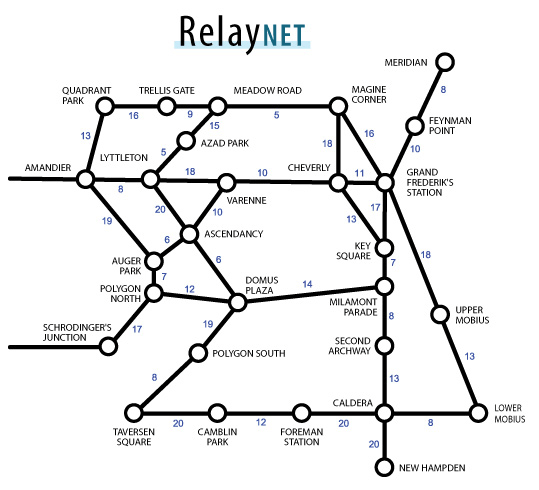
1. Third Power hackers were accessing computer servers located at the subway stations throughout the city. Exactly which servers were compromised is still unknown (each subway station houses one server, and is connected to other servers in a network similar to that of the subway system itself).
2. It is known that all of the messages were first entering the network at KEY SQUARE station (SigInt believes that the messages are being transmitted from the nearby Centre for Reality Research). From there, the hackers were carefully choosing which servers through which to route the messages (trying to use as many compromised machines as possible to minimise the chance of detection).
3. While we are still trying to discover WHERE the messages were being sent (i.e. which station/server was the final destination), with the aid of Academy CRT member Kurt McAllister, we recovered the following information about five of the messages transmitted: the times (in milliseconds) that the following five messages were bouncing around the network servers before reaching the final destination.
* Intercept 1: 60 ms
* Intercept 2: 48 ms
* Intercept 3: 57 ms
* Intercept 4: 46 ms
* Intercept 5: 59 ms
4. Police also have a network map (see image below) which lists the transmission times between servers on the network.
5. A complication is that messages can loop between servers in any fashion, possibly visiting servers more than once. However, as with normal routing, once a message reaches the destination server, it stops (i.e. it would not have bounced away from the destination server).
6. Knowing that all five messages originated from KEY SQUARE, and the above transmission times from KEY SQUARE to the destination, each message, individually, may have ended up at several possible stations. However, we believe that whichever station is reachable by the most of the five messages is the destination server to which the hackers were sending their messages.
7. Along with discovering the destination server of the messages, we also need to know which of the other servers were compromised and used to relay the messages to the destination server - this information may help us decrypt the messages we have intercepted. It is vitally important that we find the correct destination; guesses will not do, as we cannot afford to mount simultaneous assaults on multiple targets in Perplex City.
Message to readers on Earth: All members of Operation Bayonet are at full capacity. We require your assistance to discover the destination of the Relaynet intercepts. Please liaise with Kurt McAllister.