Backdoor: Difference between revisions
| Line 366: | Line 366: | ||
====Config 10: Nanoscale imager==== | ====Config 10: Nanoscale imager==== | ||
zone mount | '''Configuration:''' zone mount - - - / - switch pread - - / - - switch - cache / - - - switch rotate / - - - - rotate | ||
'''Command Path:''' zone, mount, pread, switch, switch, switch, rotate, rotate, cache | |||
[[Image:Backdoor message8.JPG]] | [[Image:Backdoor message8.JPG]] | ||
Revision as of 11:39, 2 July 2006
Summary
After discovering that V called someone at the Academy's Crypto Department, Caine heads over to Crypto to investigate. He runs into his friend Neville Clark, who is talkative, if obfuscating. The Cube Hunters entice Nev into sharing more information by giving him a puzzle, designed by jbd, to solve. Nev takes the bait, and gives us a backdoor that leads to a gridded file system.
Dragging the commands onto the grid to create various configurations yields a series of log snippets. Some of the logs resemble the Perplex City Errorlogs that were found before the puzzle cards were released.
The interface can be accessed at the following URL:
http://events.perplexcity.com/gateway/commandinterface/index.html
As of 12:36, 1 July 2006 (PDT), the puzzle is still being worked on. Join us in #syzygy, or see the discussion on the Talk page or at Unforums.
Commands
Through the combined work of jalapenodude, pelrun, and jbd, #syzygy has determined that the commands appear to work as follows:
The program pointer starts in upper left corner.
Directions:
popen - east pread - west mount - se pwrite - e switch - se (Are you sure, goes NE on config 5 below?) copy - s flush - s
'rotate' does something different depending on where it is executed, but also (sometimes?) where it comes from. Here are some directions that occur:
e e e e s s ne n n s e n ne n s ne n ne n s ne n ne n n
However, it is possible for r3c5 to go north if entered from the west, for example.
The same goes for 'zone':
e e e w s s w w n n e e e n w n w w n n n w w n n
'end' ends execution whenever it gets hit on a specific error message. It is very good for testing where the code is going. 'cache' seems to only work as an end point. 'run' can go anywhere that the program pointer isn't reaching.
Configurations
Here are the various configurations and logs that have been discovered.
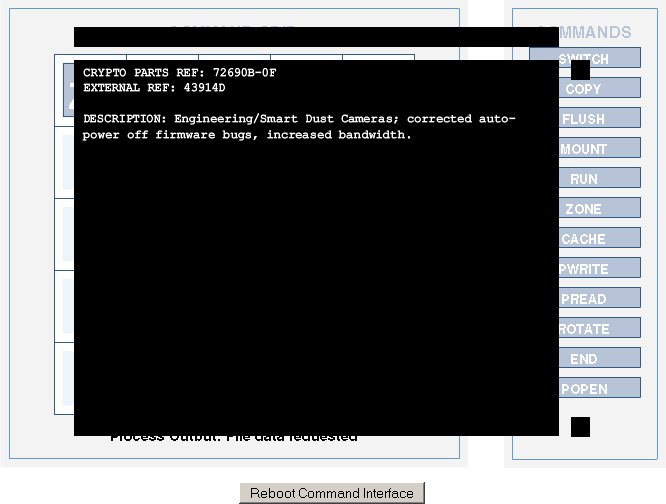
Config 1: Smart Dust Cameras
Configuration: zone, mount, run, rotate, rotate/ - - popen, zone, cache
Command path: zone, mount, popen, zone, rotate, rotate, cache
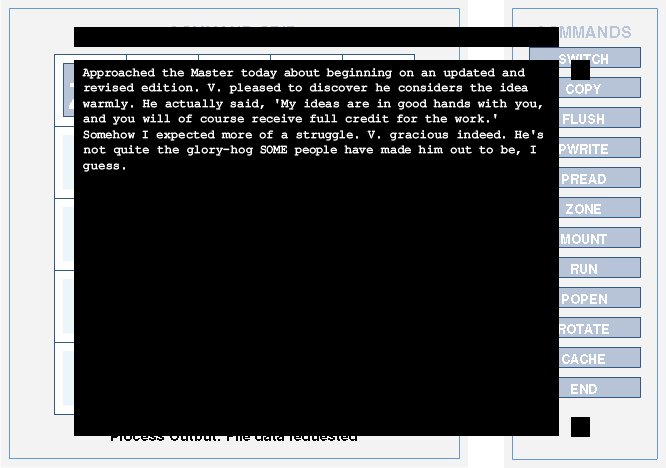
Config 2: Approaching the Master
Configuration: zone mount run rotate rotate/ - - popen rotate cache/ - - - - -
Command Path: zone, mount, popen, rotate, rotate, rotate, cache
Alternate Configuration: zone mount run pwrite cache/ - - popen rotate -
Command Path: zone, mount, popen, rotate, pwrite, cache
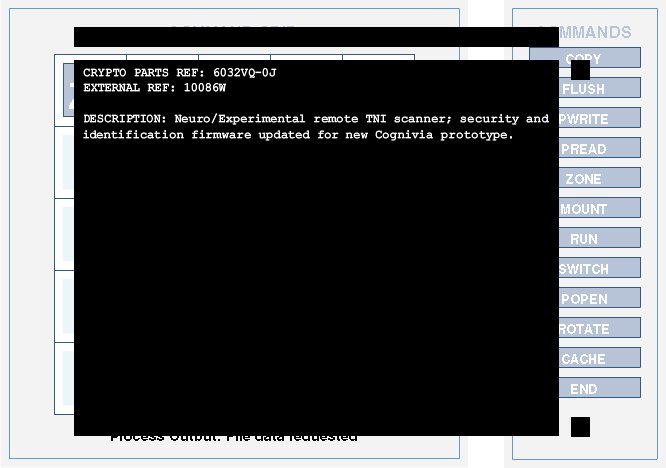
Config 3: Neuro Scanner
Configuration: zone mount run switch -/ - - popen rotate cache / - - - - -
Command Path: zone, mount, popen, rotate, switch, cache
Alternate Configuration: zone mount run - -/ - - switch cache -/ - - - rotate -
Command Path: zone, mount, switch, rotate, cache
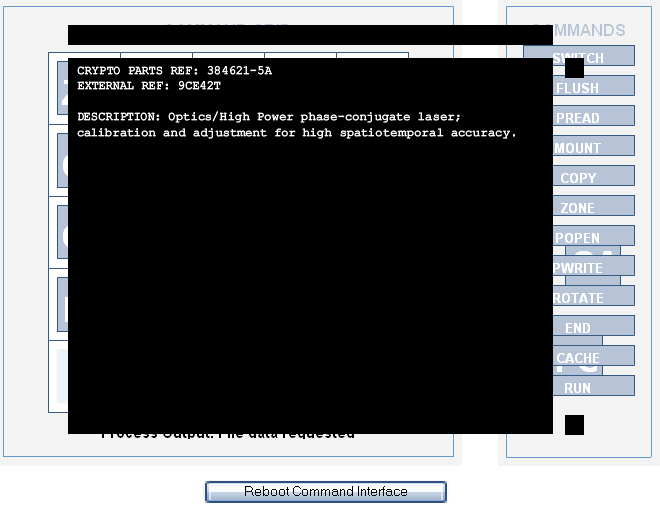
Config 4: Laser
Configuration: zone mount run -- –/copy zone zone cache --/copy pwrite rotate -- --/copy rotate -- -- --/rotate -- -- -- --
Command Path: zone, mount, zone, zone, copy, copy, copy, rotate, rotate, pwrite, rotate, cache
Config 5: Sphere
Configuration: zone mount run -- / copy zone zone cache - / copy pwrite rotate -- / copy rotate --- / switch ----
Command Path: zone mount, zone, zone, copy, copy, copy, switch, rotate, pwrite, rotate, cache
Config 6: Gatehouse 24
Configuration:' Zone Mount Run -- -- / -- -- Copy Switch Flush / -- -- Pwrite Rotate Rotate
Command Path: zone, mount, copy, pwrite, rotate, switch, rotate, flush
Alternate: zone mount run switch flush / ---- ---- pwrite rotate rotate
Command Path: zone, mount, pwrite, rotate, switch, rotate, flush
(The original configuration runs in the order zone-mount-copy-pwrite-rotate-switch-rotate-flush. The alternate configuration runs in the order zone-mount-pwrite-rotate-switch-rotate-flush. I merely managed to cut out copy, but because of the directional order of the code I had to change the places of the commands.)
Nb. it also works if you substitute Pwrite with Popen or Rotate, the same result is yielded.
When this configuration is run, a message Operation in progress appears. The screen then distorts and wavers. Finally, a log appears. Discussion on Unforums suggests that the logs may rotate, or appear randomly.
Log 1
[ GATEHOUSE 24 ]
:: start 143805 +000000
:: start 143805 +000000
:: archive location { dev 7 }
:: index { yes }
:: retention { 9 }
:: processing time { 0.53 }
::
A
// labeled A;
// triangulated location mapped;
// passive badge { present }
// badge query { friedberg, i {119yr} }
You really said that [?]
// preliminary review complete
B
// labeled B;
// triangulated location mapped;
// passive badge { present }
// badge query { carrick, h {624yr} }
I was hungry [!] I'm not diplomatic when I'm starving [.]
// preliminary review complete
// 45% positive emotional state
// cross reference surveillance footage
{ extrapolated: badge {line 16} extracted }
{ gatekeeper system 24;
active badge interrogated, passed }
FRIEDBERG, I
I bet you fifty lecks your stuff is wiped when you get back [.]
// preliminary review complete
CARRICK, H
Hah [,] I'd like to see him even try [.]
// preliminary review complete
[ LOG EXCERPT ENDS ]
Log 2
[ GATEHOUSE 24 ]
:: start 055814 +000000
:: start 061055 +000000
:: archive location { dev 7 }
:: index { yes }
:: retention { 9 }
:: processing time { 0.53 }
::
A
// labeled A;
// triangulated location mapped;
// passive badge { present }
// badge query { porta, c {112yr} }
Where have you been [?]
// preliminary review complete
B
// labeled B;
// triangulated location mapped;
// passive badge { present }
// badge query { bazeries, l {520yr} }
So I'm a little late [.] Relax [.]
// preliminary review complete
// 45% positive emotional state
// cross reference surveillance footage
{ extrapolated: badge {line 16} extracted }
{ gatekeeper system 24;
active badge interrogated, passed }
PORTA, C
We have to hurry and get this thing done [.]
// preliminary review complete
BAZERIES, L
Is he here yet [?]
// preliminary review complete
PORTA, C
I think so [.] Let's hurry [.]
// preliminary review complete
BAZERIES, L
I hope there's coffee [.]
// preliminary review complete
PORTA, C
Focus on the project [,] dunderhead [.]
// preliminary review complete
[ LOG EXCERPT ENDS ]
Log 3
[ GATEHOUSE 24 ]
:: start 192355 +000000
:: start 192401 +000000
:: archive location { dev 7 }
:: index { yes }
:: retention { 9 }
:: processing time { 0.53 }
::
A
// labeled A;
// triangulated location mapped;
// passive badge { present }
// badge query { ashford, r {737yr} }
Hey [,] wait up [.]
// preliminary review complete
B
// labeled B;
// triangulated location mapped;
// passive badge { present }
// badge query { wooster, m {019yr} }
Oh [,] sorry [.] Hard meeting today [.]
// preliminary review complete
// 23% positive emotional state
// cross reference surveillance footage
{ extrapolated: badge {line 16} extracted }
{ gatekeeper system 24;
active badge interrogated, passed }
ASHFORD, R
Do you ever wonder [...]
// preliminary review complete
WOOSTER, M
Don't say it [.]
// preliminary review complete
ASHFORD, R
I know [,] I know [.] No place is safe [.]
// preliminary review complete
[ LOG EXCERPT ENDS ]
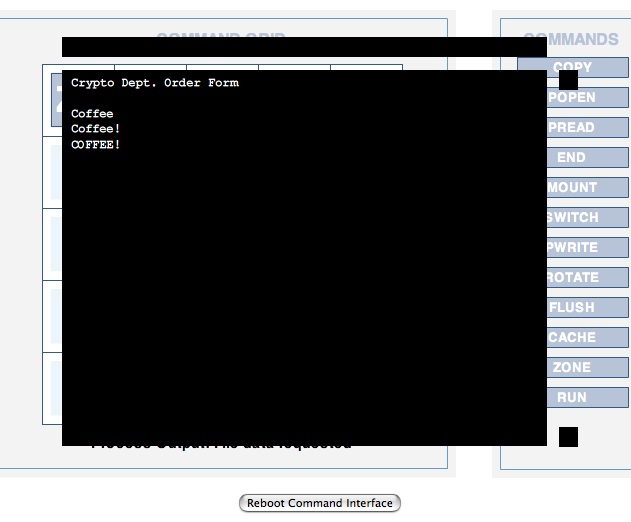
Config 7: Coffee
Configuration: zone mount run switch - / - - pwrite rotate flush / - - - cache zone
Command Path: zone, mount, pwrite, rotate, switch, flush, zone, cache
Config 8: Kiteway disrupting the department
Configuration: zone mount - - - / - switch pread - - / - - switch cache - / - - - rotate -
Command Path: zone, mount, pread, switch, swtich, rotate, cache
To: 55321801 FROM: MANSOOR H. Kiteway's programs are disrupting the entire department. Breeding hostility and distrust among amicable colleagues. The man doesn't belong here anymore, why can't he keep his damned pet projects in his own office? Crypto is mine now, not his. Well, here are the metrics to show he's not minding his own business. Number of times Kiteway has visited dept. offices this year: 78 And in 268: 129 And in 267: 23 Dept. suspicion level on the Howe-Panntonin Index: 8.8 And in 268: 7.3 And in 267: 4.5 Suspect the man has his own agenda and isn't sharing with the proper channels, for example me and you. Suspect he is subverting the time and resources of my faculty without consulting me ahead of time. Behaving as though he can't trust his own senior fellows. Ridiculous. How long must we put up with this childish rigmarole?
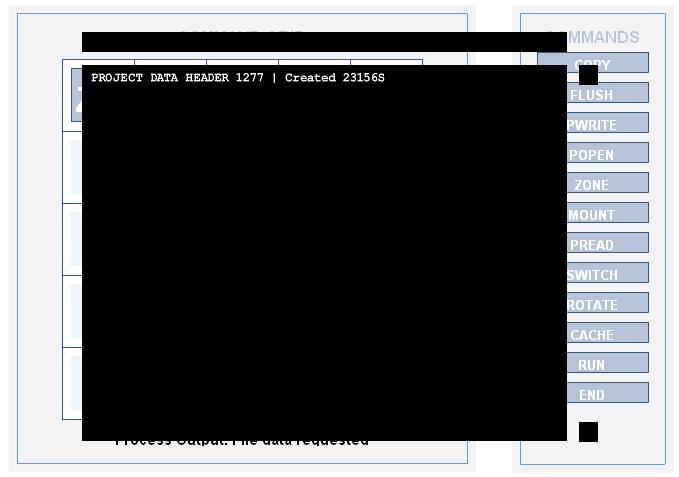
Config 9: Project Data
Configuration: zone mount - - - / - switch pread - - / - - switch - - / - - - switch cache / - - - - rotate
Command Path: zone, mount, pread, switch, switch, switch, rotate, cache
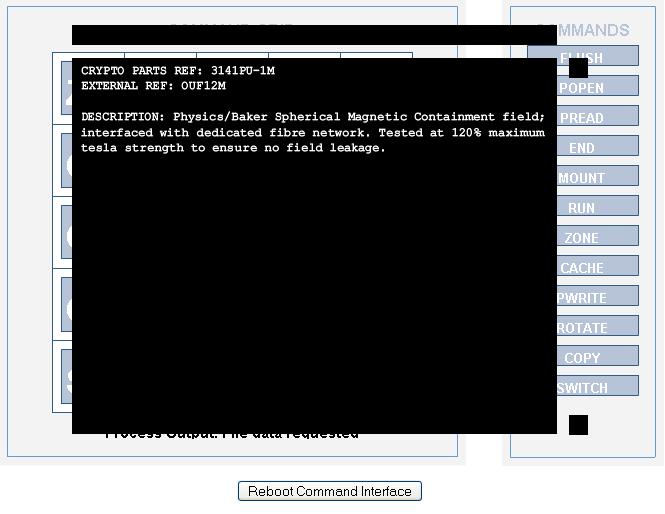
Config 10: Nanoscale imager
Configuration: zone mount - - - / - switch pread - - / - - switch - cache / - - - switch rotate / - - - - rotate
Command Path: zone, mount, pread, switch, switch, switch, rotate, rotate, cache
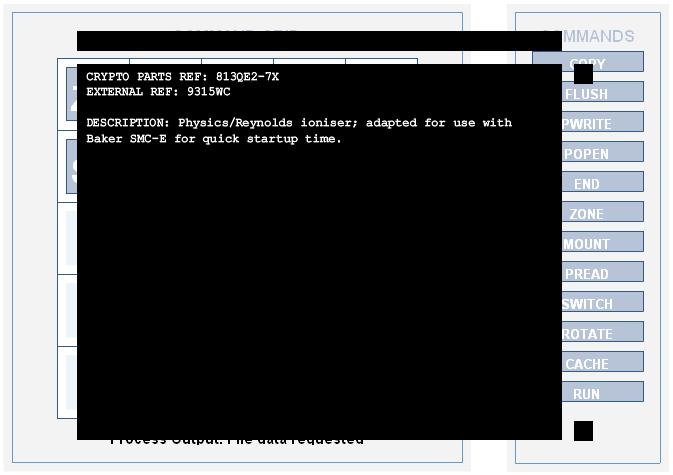
Config 11: Reynolds ioniser
zone mount -- -- -- / switch pread pread -- -- / -- switch -- -- -- /-- -- switch switch cache / -- -- -- rotate rotate
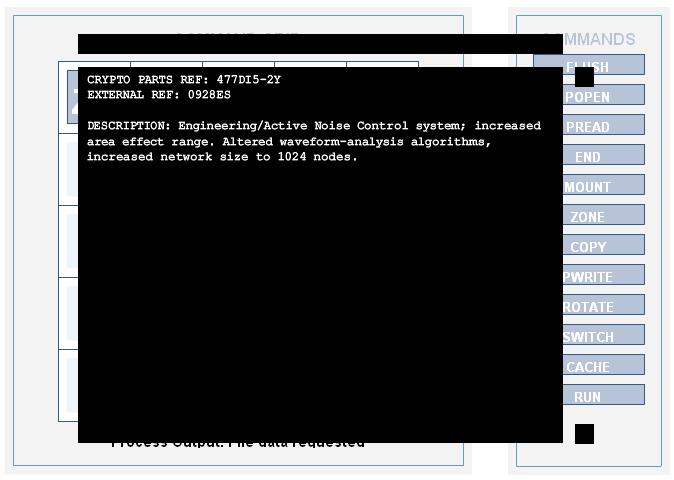
Config 12: Noise control system
zone mount -- -- -- / -- copy zone switch -- / -- pwrite switch rotate cache / -- -- -- rotate --
Historical Cryptographers
Some of the names mentioned in the logs share the names of historic cryptographers and mathematicians.
- Bazeries
- French military cryptographer, the 'pragmatic man of cryptology'. Famous for breaking the French 'Great Cipher' created in the 17th century.
- Porta
- Giovanni Battista Porta, Italian cryptographer and inventor of the Della Porta cipher - a polyalphabetic cipher with keyword.
- Ashford
- the name of the village in Kent where John Wallis, 17th century mathematician, was born. He wrote among other things, about the quadrature of curves, logic, theology and cryptography.
- Carrick
- the name of a Windows-based encryption application, designed by cryptographer Bruce Schneier.